Over the past few years, we’ve seen ransomware rise in popularity. It has evolved from encrypting data for ransom to hacking backups and data theft to expose it or sell it unlawfully as part of “double extortion” schemes. The cybercriminals perpetrating these attacks have evolved from disorganized splinter groups and individuals to highly sophisticated start-ups offering ransomware-as-a-service to target everything from SMBs to software supply chains. Ransomware attacks in 2021 were massively successful and profitable predicting an ugly trend for 2022 and beyond: Ransomware isn’t going anywhere.
Kela’s analysis of the dark web reveals that ransomware is still the top threat for businesses with the perfect ransomware victim being described as an organization “with revenue of more than 100 million USD”. Ransomware attackers also prefer to buy access that includes domain admin rights as well as entry into remote desktop protocol (RDP) and Virtual private network (VPN) services. With the evolution of ransomware, ransomware infection is no longer the end goal of the attack but only one component in the attack that has been designed to elicit blackmail payments from victims. Malware in this area includes WannaCry, NotPetya, Ryuk, Cerber, and Cryptolocker.
Here are 4 unsettling ransomware forecasts in 2022 and beyond:
Cybercriminals will get smarter, better and faster
We saw malicious code being slipped into a routine software update in the SolarWinds attack. Since then, cybercriminals continued to find new and innovative ways to penetrate networks and circumvent end-point solutions. A new strain of malware was identified in 2021 that capitalizes on the remote work environment that is capable of encrypting an entire corporate system in less than 3 hours.
The volume of attacks will continue to increase
Considering the record-breaking ransoms paid by the likes of Colonial Pipeline, Air India, and CWT Global, why would ransomware attackers stop now? Ransomware is a lucrative business that attracts more cybercriminals into its criminal enterprise daily – no hacking skills required. Ransomware attackers are no longer anonymous, hooded characters online, they’re disgruntled employees and angry patients. With ransomware-as-a-service, anyone with a grudge can now wield a ransomware attack.
Attack vectors will get more sophisticated
Cybercriminals are deploying more sophisticated attack vectors and corrupting data in new and unexpected ways. An example is Lockfile with its unique intermittent encryption approach to ransomware which evades detection of many standard detection tools that do not check the integrity inside file content. We expect to see more attack vectors that corrupt data in clever ways to thwart basic analytics tools.
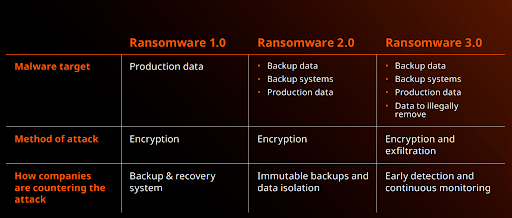
Backups are the new target
Ransomware attackers’ end goal is to make organizations as desperate as possible by doing as much damage as possible to be able to demand as much ransom as possible. Erasing and encrypting backups is a surefire way to obstruct any attempts by organizations to recover. The problem is that standard data protection leaves organizations’ backups vulnerable and cybercriminals know it which means that in 2022, relying on backups that have not been analyzed to ensure recovery from ransomware is no longer a viable strategy.
A robust cyber resiliency strategy is crucial to ensure your organization is prepared for ransomware or other cyber security threats. If you’re ready to adopt a next-gen data management and backup solution that incorporates zero trust principles, get in touch.
Ransomware Readiness:
An In-Depth Evaluation Guide
If you found this post interesting, you might enjoy these too:
Streamline data backup and recovery with Cohesity’s comprehensive SaaS solution
Case Study: Onboarding Cohesity Improves Stage2Data’s Top and Bottom Lines



